Clones in the Cloud: The Deceptive GitHub Login Scam
Fresh Year, Fresh Threat. This time targeting the devs. How to protect yourself from login scams.
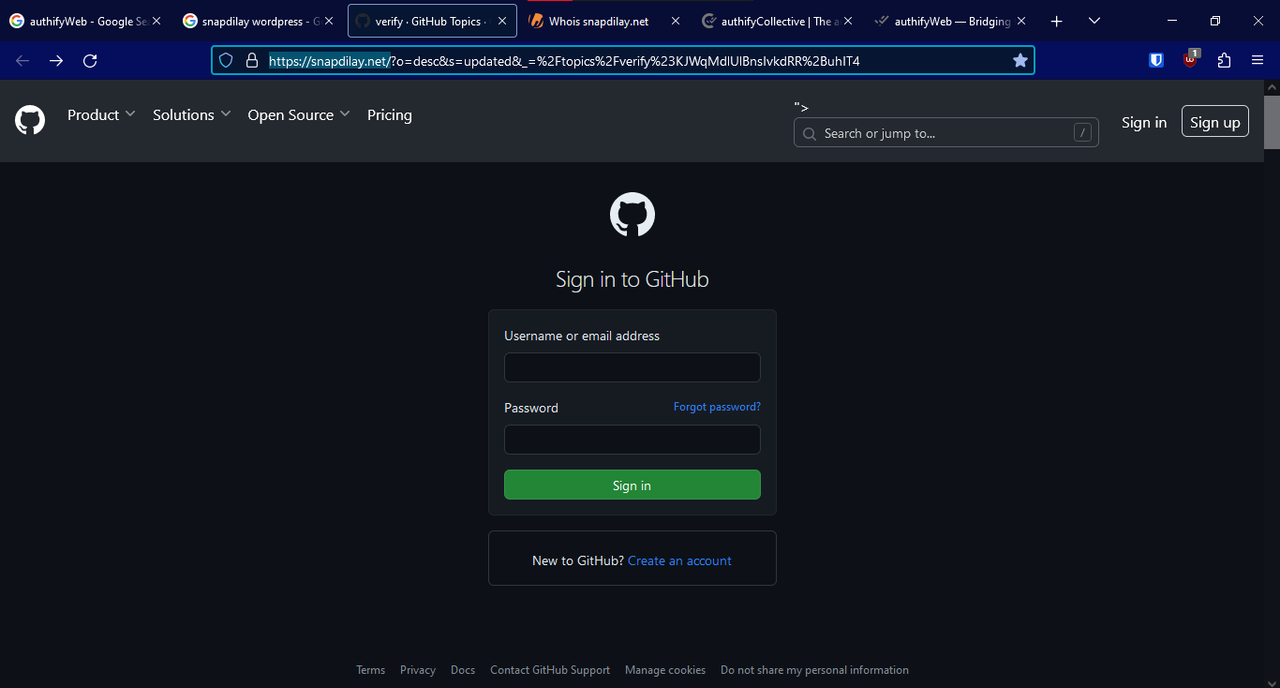
GitHub, the place where collaboration happens and where development and innovation thrive, is the latest target for impersonation scams. A cunning phishing website has surfaced that resembles the official GitHub website and prompts developers to login.
These imposter login pages often appear as near-perfect replicas of the genuine GitHub interface. They mimic the familiar layout, branding, and logo. However, beneath this familiar surface lies a deceptive phishing scam that intercepts the developer’s username and password.

The site is just 3 weeks old, and there are already multiple links indexed in Google results. We tested it on other search engines, including DuckDuckGo, Yandex, and Brave Search, but none are indexing any of these phishing links yet. But search engines like Yahoo, Bing, and Ecosia index the main page of the scam site, which itself is a clone of a website called Partoo.
Danger Lurks behind the Non-existent pages
These pages don’t exist on the website itself; they could only be accessed from a search result page or through a direct link. This makes the scam more scary; unless the user explicitly searches for a “specific term,” it doesn’t appear at all, staying undetected by scam verification services. We tested the link with a few scam detection services, and all showed it to be safe. (They can’t be blamed; no scam pages exist on the website itself.)
Example URL: https://snapdilay.net/?_=%2Ftopics%2Fpacman%23KJWqMdlUlBnsIvkdRR%2BuhIT4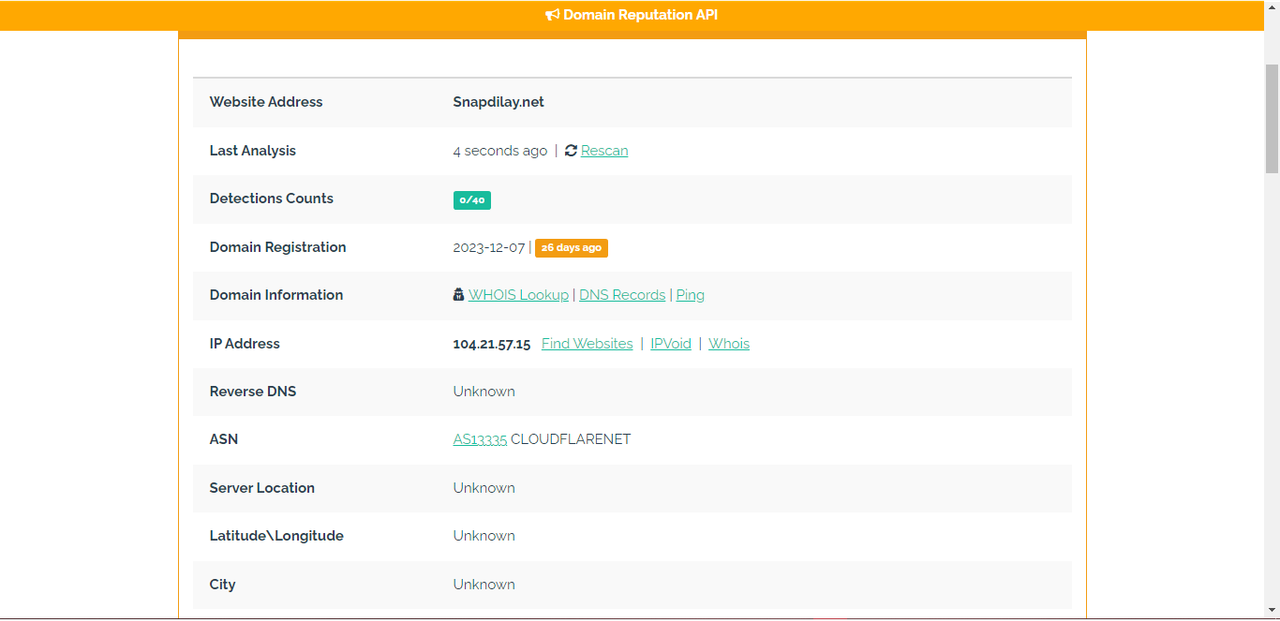

Possibility of how the scam could unfold:
Deceptive Links: Lurking within emails, chat messages, or even social media posts, these links pretends as legitimate redirects.
Unsuspecting Commoners: Users searching for open-source tools as an alternative to other proprietary software could end up being the target of these scams.
Red Flags That Should Raise the Alarm.
Typos and Inconsistency: Pay close attention to inconsistencies, such as subtle errors in spelling, grammar, or images that betray their fraudulent nature.
Security Certificates: Your browser may warn you about invalid security certificates or insecure connections. (Again, this site had a valid HTTPS certificate.)
Suspicious URLs: Always, always double-check the URLs, especially if you are using the in-app webview.
What you could do to avoid such scams?
- Staying vigilant and adopting security best practices are crucial to safeguarding your digital ecosystem.
- Beware of unsolicited messages and mail. Double-check URLs before interacting with them.
- Enable 2FA and keep it as a minimum requirement.
- Report suspicious sites and unauthorized activities on you account.
Together, we can combat these wicked scams and preserve the integrity of the free and open web. Stay vigilant and spread awareness.
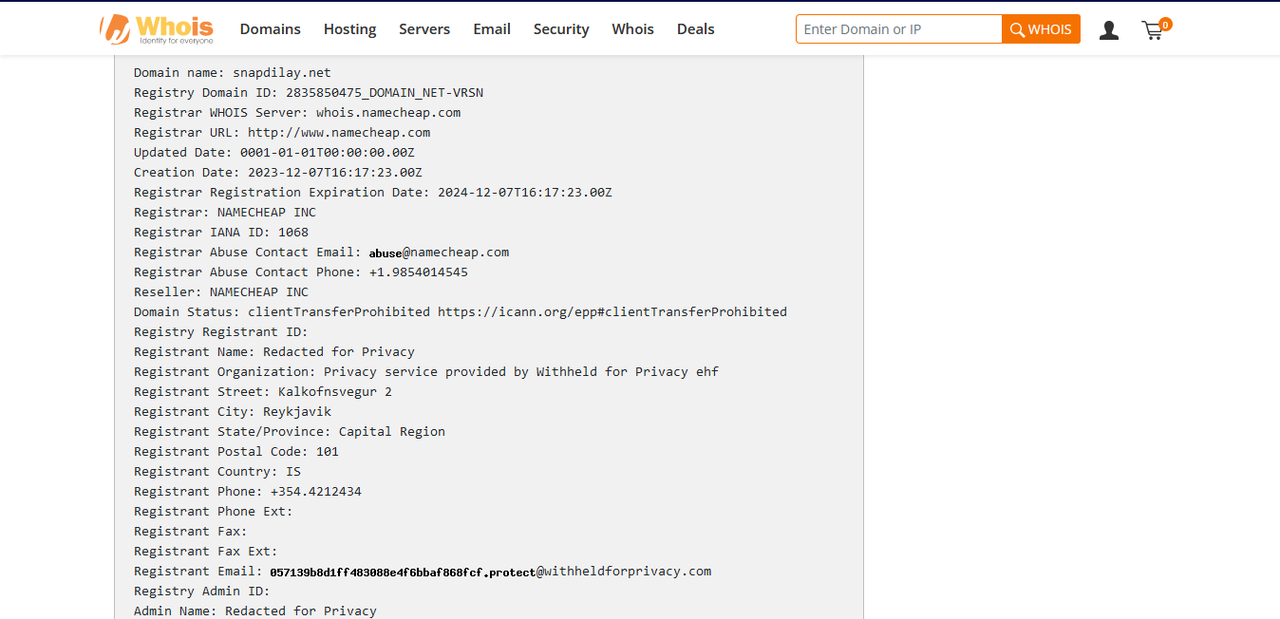
Update: Namecheap has suspended the domain
https://x.com/Namecheap/status/1743365445313257883
Read More: Phishing Beyond GitHub – How This Domain Mimics Any Site
Your contributions help us sustain this project.
Together, We Can Achieve Great Things
Other ways to give: Patreon, Corporate Sponsorship
This content and its accompanying images are licensed under a Creative Commons Attribution-NoDerivatives 4.0 International License. You are free to share and redistribute this content and its images in any medium or format, as long as you give appropriate credit and do not modify the content in any way.